Analysis of Windows kernel information disclosure from CVE-2017-0167
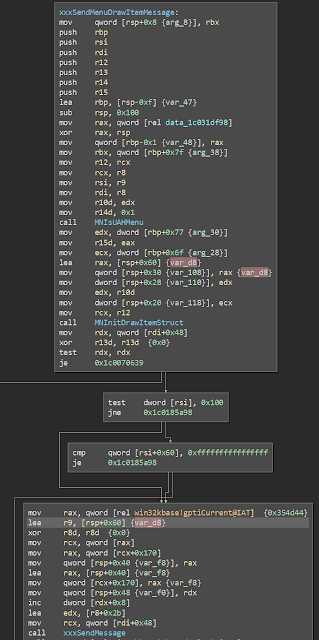
In CVE-2017-0167 Google Security found a Windows kernel information disclosure through the user mode callback user32! fnINLPUAHDRAWMENUITEM . A sub-function of CreateWindow issues a syscall that in return calls a user mode callback with a copy of a data structure from kernel space. This data structure is copied from the stack while executing in the kernel, and a portion of that structure is uninitialised, meaning that it can contain stale stack data that can be used to glean information from the kernel in order to defeat protections like KASLR. Google Security included a brief write up of the bug and even supplied a PoC to demonstrate it, but didn't go into detail about how the bug actually works. Given that the bug is actually pretty straightforward I think it's worth going into a little bit deeper and getting a better idea of what's going on under the hood and how an oversight as simple as not initialising a structure lead to a kernel to userspace information disc...